Digital currency mining has been installed on sites and web servers recently, using a guest's program as a vehicle to process mining exchanges.
It utilizes clueless guests' PC assets yet sends any benefits determined straight to a wallet outside of the guest's control.
It's an asset depleting pattern that is just expanding. Since September 2017, more than 5,000 sites have been installed with Coinhive, a Monero digital money excavator. Ransomware has gradually been dropping off from that point forward, after a moderately ruthless year in 2017 which highlighted WannaCry and NotPetya, and in its place it appears to be obvious to cybersecurity experts that "cryptojacking" is quick turning into 2018's malware of decision, having come to over 500 million clients' gadgets.
By mining in a web program, Coinhive claims this a suitable strategy for website admins to battle the utilization of promotion blockers, for example, "uBlock Origin," which deny sites of valuable advertisement movement income—income that numerous destinations depend on keeping in mind the end goal to keep working.
Some prominent destinations have toyed with coordinating crypto mineworkers into their locales, quite The Pirate Bay and other deluge destinations.
This is the new scene, an approach to not really go straight for a man or organizations' assets straightforwardly, or hold them deliver, but instead covertly introducing programming or running a content on their web program which depletes their PC assets and increase their energy costs.
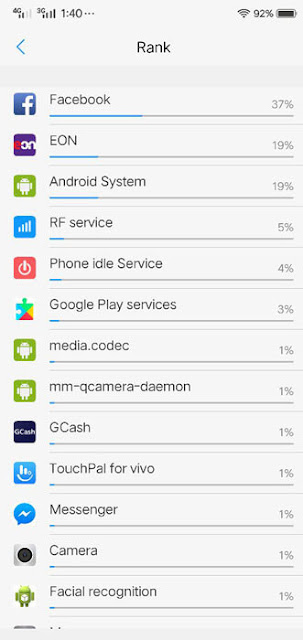
The most straightforward and slightest undermining type of cryptojacking is the point at which a site executive or individual who controls a web server embeds a little Javascript mineworker into a website's center spine. They may be forthright about it, or they may clandestinely endeavor to mine digital currency utilizing your gadget. When you visit this server, your program runs the content and starts mining at extraordinary cost to your PC's energy.
The most effortless approach to circumnavigate this kind of cryptojacking is to introduce a promotion blocker which has expressly prompted they have added known cryptojacking administrations to their piece list. It's not secure however, and for a more total administration, it's best to hinder all contents in your web program utilizing something like "No Script" or "uMatrix."
It will require investment to get used to the web again as you peel it back—requiring a touch of play to get Javascript rich destinations to work legitimately. However, it's likewise somewhat of a stun to see exactly what your most loved site is endeavoring to keep running on your PC, including numerous following contents and data harvesting scripts.
.
It's considerably more hard to recognize crypto diggers that have been inserted into the source code of an application which you run locally on your PC or gadget. It's essential, in this way, to guarantee your applications are dependably a la mode, since refreshes are typically loaded with security patches.
Be that as it may, programmers can capture the download connection of locales, pushing their own variants of utilizations which have been changed.
The most ideal approach to battle this is to dependably check the hash of the record you are downloading. It's somewhat extraordinary for each stage, yet a brisk inquiry will demonstrate to you best practices to do this, and once you begin, it ends up less demanding to do going ahead.
In this situation, a programmer would access an organization or home server and endeavor to pick up root get to, which empowers them to take control of the machine. With control of the machine, they are allowed to introduce crypto diggers and set the yield addresses as their own.
You may see unusual utilization from a home server you're running, or you may see a product that shouldn't run. It's critical to have a decent comprehension of system security in case you're running a server, since cryptojacking is quick turning into the most gainful technique for programmers to separate an incentive from you.
Some filtering programming should see something isn't right. If not, it will probably appear in the procedures running.
It's anything but difficult to end up smug with regards to web program and PC wellbeing. Every single real program are endeavoring to execute new security highlights, yet frequently these highlights originate from the best program additional items, which means you could be secure from cryptojacking now on the off chance that you have the correct additional items introduced.
Executing contents in your web program will murder about all crypto diggers. Be that as it may, in doing as such, numerous locales may end up hard to utilize at first, until the point when you allow the site the capacity to run the contents you require.
It can now and again be a speculating diversion, and you may even wind up empowering a digital money excavator accidentally. Coinhive's talk that cryptojacking could supplant promoting as a wellspring of income appears to be lost right now, since as a rule it's a noteworthy pay cut for sites.
Maybe as Google executes their local promotion blocker, crypto mineworkers in destinations will simply continue expanding and even turn into a honest to goodness route for site proprietors to take income. For the present, however, it's remark out of your framework, and a content blocker is the simplest way.
It utilizes clueless guests' PC assets yet sends any benefits determined straight to a wallet outside of the guest's control.
It's an asset depleting pattern that is just expanding. Since September 2017, more than 5,000 sites have been installed with Coinhive, a Monero digital money excavator. Ransomware has gradually been dropping off from that point forward, after a moderately ruthless year in 2017 which highlighted WannaCry and NotPetya, and in its place it appears to be obvious to cybersecurity experts that "cryptojacking" is quick turning into 2018's malware of decision, having come to over 500 million clients' gadgets.
HISTORY OF CRYPTOJACKING
Program cryptographic money mining has been examined in digital money hovers for quite a long time, yet rapidly wound up out of date as GPU influence turned into the Bitcoin standard. In any case, it was Coinhive that made the main business interface with a plan to supplant promoting income, utilizing a CPU which can mine Monero.By mining in a web program, Coinhive claims this a suitable strategy for website admins to battle the utilization of promotion blockers, for example, "uBlock Origin," which deny sites of valuable advertisement movement income—income that numerous destinations depend on keeping in mind the end goal to keep working.
Some prominent destinations have toyed with coordinating crypto mineworkers into their locales, quite The Pirate Bay and other deluge destinations.
IMPROVEMENTS IN CRYPTOJACKING
Since late-2017, programmers have taken the thought behind Coinhive and assaulted some accidental servers, projects or "bot" machines, releasing crypto diggers and hindering the legitimate proprietors by basically taking their assets. One of the biggest such illustrations was back in January 2018 when programmers snatched around a fourth of a million dollars in Monero, mined on Oracle's Weblogic Servers—a prominent organization's framework.This is the new scene, an approach to not really go straight for a man or organizations' assets straightforwardly, or hold them deliver, but instead covertly introducing programming or running a content on their web program which depletes their PC assets and increase their energy costs.
ANTICIPATION: SAFETY and SECURITY TIPS
There are a few things you can do as a client to diminish the danger of having your program or server used to mine digital currency without your assent or learning. These strategies for anticipation must match the level of assault as well as a focus by the enemy.Browser Mining
The most straightforward and slightest undermining type of cryptojacking is the point at which a site executive or individual who controls a web server embeds a little Javascript mineworker into a website's center spine. They may be forthright about it, or they may clandestinely endeavor to mine digital currency utilizing your gadget. When you visit this server, your program runs the content and starts mining at extraordinary cost to your PC's energy.
The most effortless approach to circumnavigate this kind of cryptojacking is to introduce a promotion blocker which has expressly prompted they have added known cryptojacking administrations to their piece list. It's not secure however, and for a more total administration, it's best to hinder all contents in your web program utilizing something like "No Script" or "uMatrix."
It will require investment to get used to the web again as you peel it back—requiring a touch of play to get Javascript rich destinations to work legitimately. However, it's likewise somewhat of a stun to see exactly what your most loved site is endeavoring to keep running on your PC, including numerous following contents and data harvesting scripts.
.
Application Mining
Be that as it may, programmers can capture the download connection of locales, pushing their own variants of utilizations which have been changed.
The most ideal approach to battle this is to dependably check the hash of the record you are downloading. It's somewhat extraordinary for each stage, yet a brisk inquiry will demonstrate to you best practices to do this, and once you begin, it ends up less demanding to do going ahead.
Server Mining
You may see unusual utilization from a home server you're running, or you may see a product that shouldn't run. It's critical to have a decent comprehension of system security in case you're running a server, since cryptojacking is quick turning into the most gainful technique for programmers to separate an incentive from you.
Some filtering programming should see something isn't right. If not, it will probably appear in the procedures running.
Stay Alert
Executing contents in your web program will murder about all crypto diggers. Be that as it may, in doing as such, numerous locales may end up hard to utilize at first, until the point when you allow the site the capacity to run the contents you require.
It can now and again be a speculating diversion, and you may even wind up empowering a digital money excavator accidentally. Coinhive's talk that cryptojacking could supplant promoting as a wellspring of income appears to be lost right now, since as a rule it's a noteworthy pay cut for sites.
Maybe as Google executes their local promotion blocker, crypto mineworkers in destinations will simply continue expanding and even turn into a honest to goodness route for site proprietors to take income. For the present, however, it's remark out of your framework, and a content blocker is the simplest way.